一、目标
用python的Flask库启动一个web Server,结合frida通过直接调用某段子App的方法来计算sign。
- 某段子App版本 5.5.10
二、分析
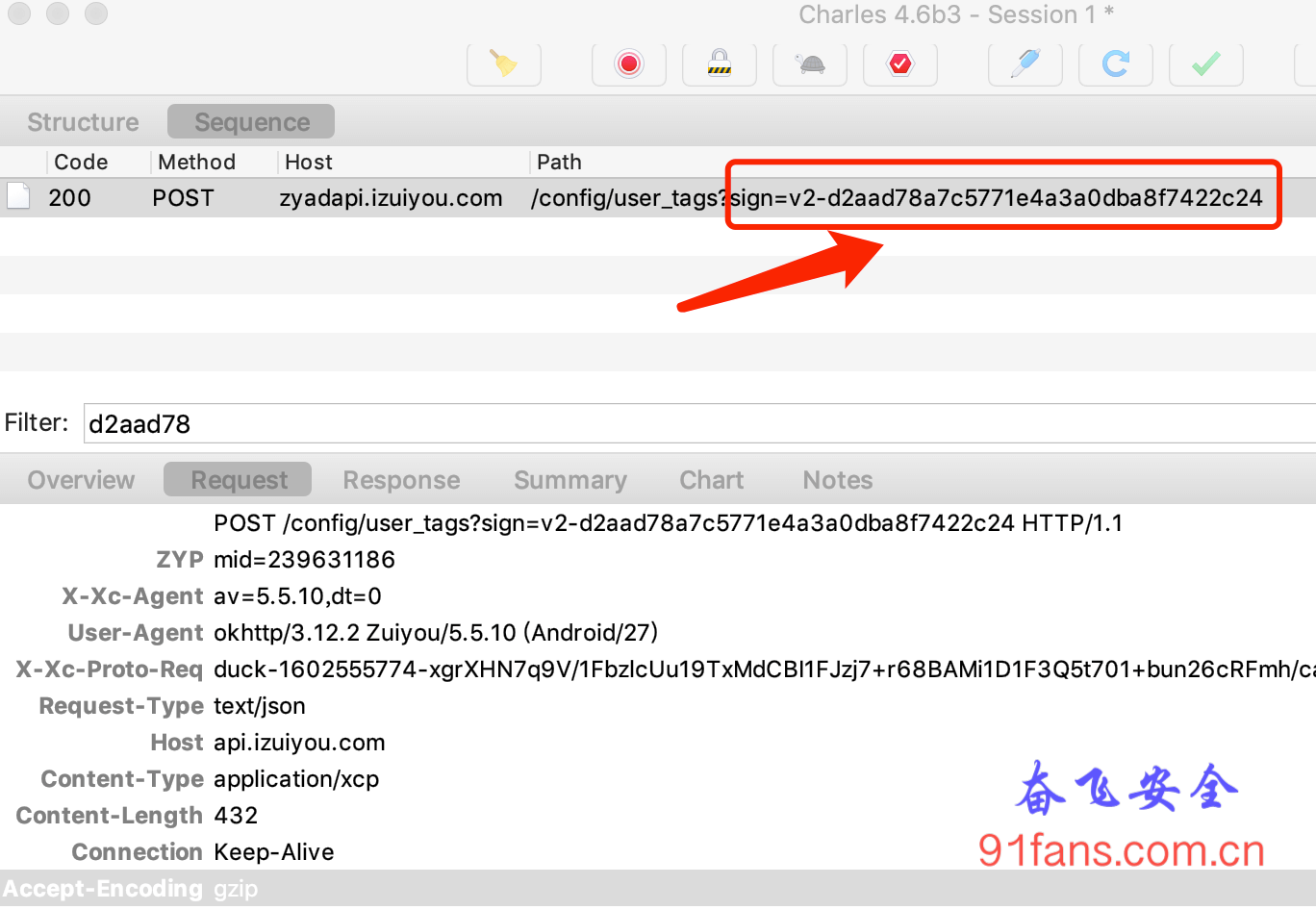
- 使用charles对目标app进行抓包,抓包结果如下:
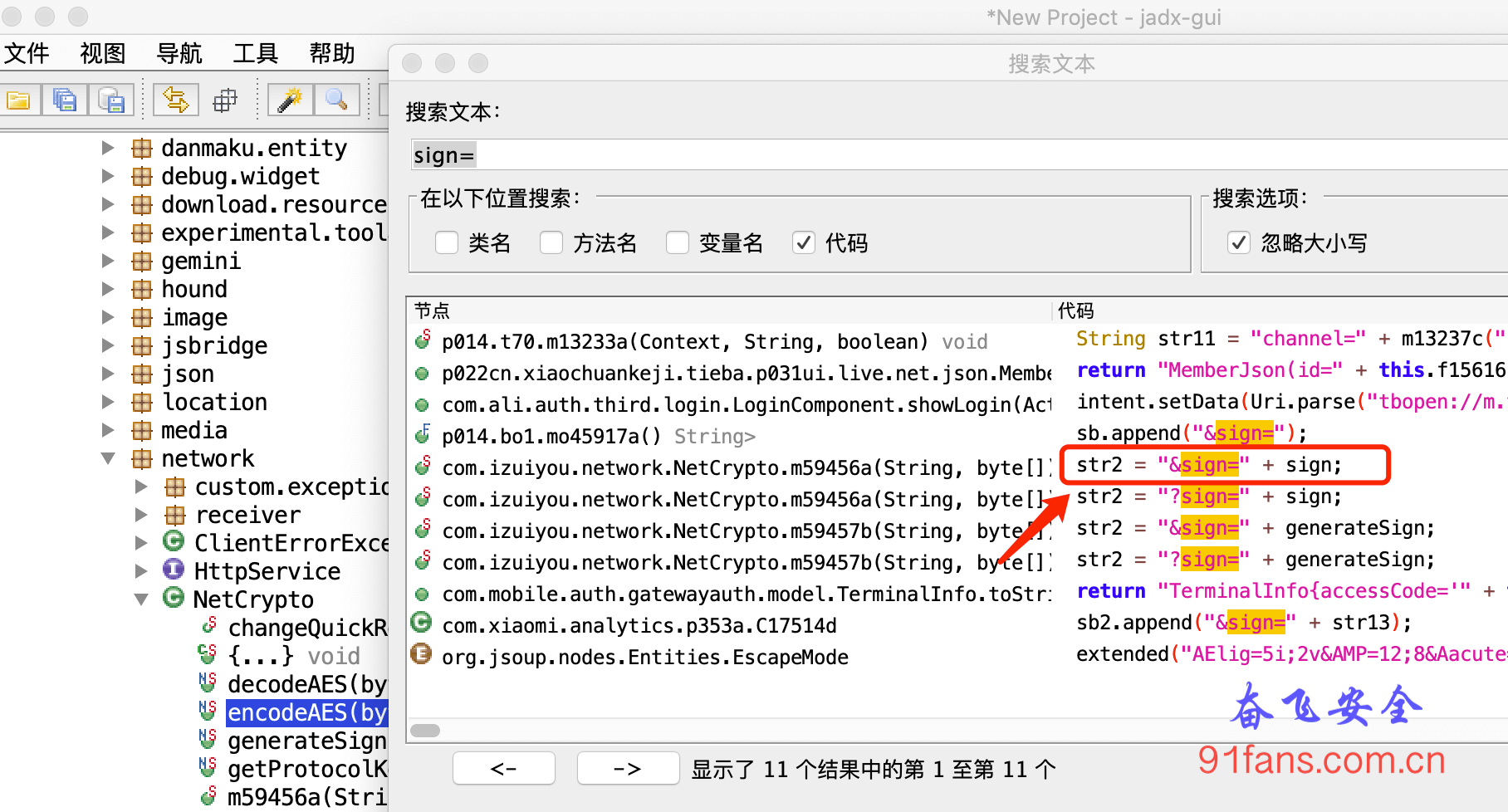
- 使用 jadx反编译某段子App的apk,然后搜索文本 sign=
- 双击之后进入到对应的代码中
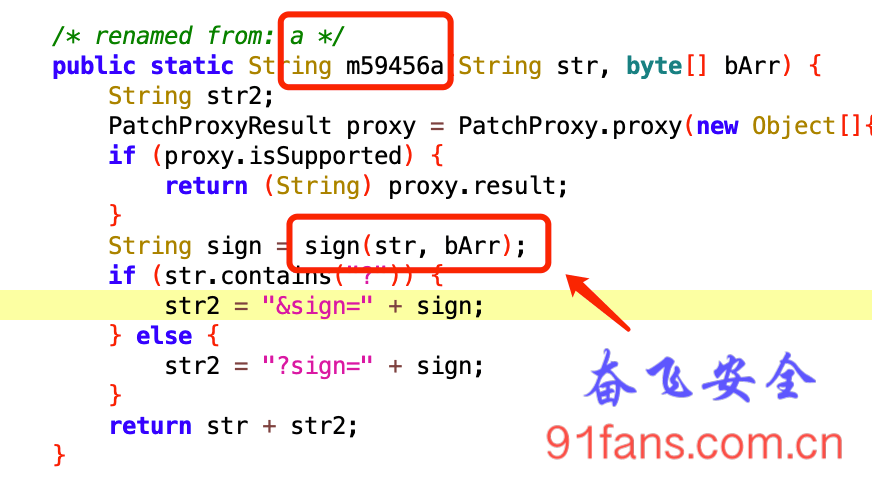
- 我们用frida来hook这个sign函数,sign函数有两个参数,String和byte[]
var ZYNetCrypto = Java.use("com.izuiyou.network.NetCrypto");
ZYNetCrypto.sign.implementation = function(arg1, arg2){
console.log("\nNetCrypto.sign\n");
console.log("str=" + arg1 + "\nbuf=" + printBytes(arg2) + "\nbuf2=" + Bytes2HexString(arg2) + "\njson=" + JSON.stringify(arg2));
var result = this.sign(arg1, arg2);
console.log("\nOut Rc=" + result);
return result;
}- 运行 python3 run.py hook, 输出结果
str=https://api.izuiyou.com/config/user_tags
buf=0x69, 0x0c, 0x47, 0x56, 0x66, 0x75, 0x75, 0x85, 0x94, 0x94, 0x34, 0x44, 0x53, 0x53, 0x63, 0x72, 0x9b, 0x9b, 0x6a, 0xa6, 0x32, 0x5e, 0x75, 0x5f, 0x53, 0x9e, 0x8e, 0x59, 0xfd, 0x41, 0xe6, 0x62, 0xf3 ....
Out rc=https://api.izuiyou.com/config/user_tags?sign=v2-d2aad78a7c5771e4a3a0dba8f7422c24签名sign的值是 v2-d2aad78a7c5771e4a3a0dba8f7422c24
- 现在我们用同样的参数直接调用 com.izuiyou.network.NetCrypto.sign 函数
app = Flask(__name__)
@app.route('/zy')
def zy_test():
global gScript
str = 'https://api.izuiyou.com/config/user_tags'
buf = bytearray([0x69, 0x0c, 0x47, 0x56, 0x66, 0x75, 0x75, 0x85, 0x94, 0x94, 0x34, 0x44, 0x53, 0x53, 0x63, 0x72, 0x9b, 0x9b, 0x6a, 0xa6, 0x32, 0x5e, 0x75, 0x5f, 0x53, 0x9e, 0x8e, 0x59, 0xfd, 0x41, 0xe6, 0x62, 0xf3 ....])
res = gScript.exports.callzyfun(str,buf.hex());
return jsonify(res);function callSignFunZy(str,buf){
var result = 'null';
console.log(str);
var arr = HexString2Bytes(buf);
Java.perform(function () {
var ZYNetCrypto = Java.use("com.izuiyou.network.NetCrypto");
var res = ZYNetCrypto.sign(str,arr) ;
result = res;
});
return result;
}
rpc.exports = {
callzyfun : callSignFunZy, // 导出名不可以有大写字母和下划线
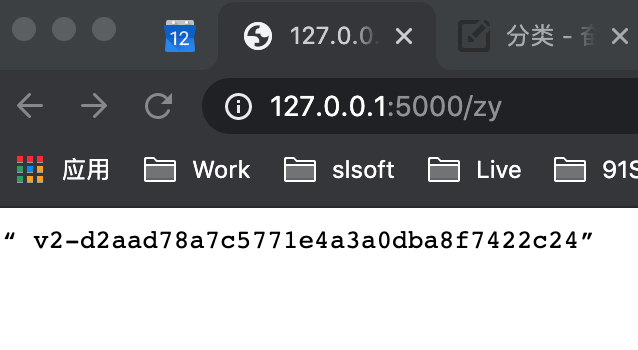
};从浏览器里访问Flask服务 http://127.0.0.1:5000/zy 可以得到一样的结果 v2-d2aad78a7c5771e4a3a0dba8f7422c24
关注微信公众号,最新技术干货实时推送